Comparing VPNs for Security in High-Risk Regions
Find the most secure VPNs for use in high-risk regions like the USA and Southeast Asia. Focus on obfuscation and strong encryption.
Find the most secure VPNs for use in high-risk regions like the USA and Southeast Asia. Focus on obfuscation and strong encryption.
Comparing VPNs for Security in High Risk Regions
Navigating the digital landscape in high-risk regions, such as the USA and various countries in Southeast Asia, presents unique challenges for online security and privacy. These regions often feature complex legal frameworks, extensive surveillance, and varying degrees of internet censorship. For anyone living in or traveling through these areas, a Virtual Private Network (VPN) isn't just a convenience; it's a crucial tool for protecting your digital footprint, ensuring freedom of expression, and maintaining access to unbiased information. But not all VPNs are created equal, especially when the stakes are high. This comprehensive guide will delve into what makes a VPN secure for high-risk environments, compare leading providers, and offer practical advice to help you choose the best option for your needs.
Understanding High Risk Regions and Their Digital Landscape
Before we dive into VPN specifics, let's define what makes a region 'high-risk' from a digital security perspective. This typically involves:
- Extensive Government Surveillance: Countries with broad surveillance programs, data retention laws, or intelligence-sharing agreements (like the Five Eyes, Nine Eyes, and Fourteen Eyes alliances, which include the USA) can compromise your privacy.
- Internet Censorship and Restrictions: Governments in some Southeast Asian countries, for example, might block access to certain websites, social media platforms, or news outlets. A VPN helps bypass these restrictions.
- Cybercrime and Hacking Threats: High-risk regions can also be hotspots for cybercriminals, making robust encryption and security features essential to protect against data theft and phishing.
- Legal Ambiguity or Hostility Towards VPNs: While VPNs are generally legal in the USA, some countries have stricter regulations or even outright bans, requiring VPNs with advanced obfuscation.
- Lack of Digital Rights Protections: Weaker legal protections for digital privacy and freedom of speech can expose users to greater risks.
The USA, while a beacon of freedom in many respects, is part of the Five Eyes intelligence alliance, meaning data collected within its borders can be shared with other member nations. This, coupled with extensive data collection by corporations and government agencies, makes strong encryption and a no-logs policy paramount. In Southeast Asia, the situation varies widely. Countries like Vietnam, Thailand, and Indonesia have implemented internet censorship and surveillance measures, while others like Singapore have more open internet policies but still emphasize data security. Therefore, a VPN for these regions needs to be robust, reliable, and capable of handling diverse threats.
Key VPN Features for Enhanced Security in High Risk Areas
When selecting a VPN for a high-risk region, certain features become non-negotiable. These go beyond basic encryption and aim to provide maximum anonymity and protection:
Robust Encryption Standards and Protocols for Data Protection
The backbone of any secure VPN is its encryption. For high-risk regions, you need the strongest available:
- AES-256 Encryption: This is the industry standard, often referred to as 'military-grade' encryption. It's virtually uncrackable by current technology.
- Secure Protocols: Look for VPNs that offer WireGuard, OpenVPN (UDP/TCP), and IKEv2/IPsec. WireGuard is known for its speed and modern cryptography, while OpenVPN is highly customizable and widely audited. Avoid outdated protocols like PPTP or L2TP/IPsec, which have known vulnerabilities.
- Perfect Forward Secrecy (PFS): This ensures that even if one encryption key is compromised, past and future session keys remain secure. Each session uses a unique key, adding an extra layer of protection.
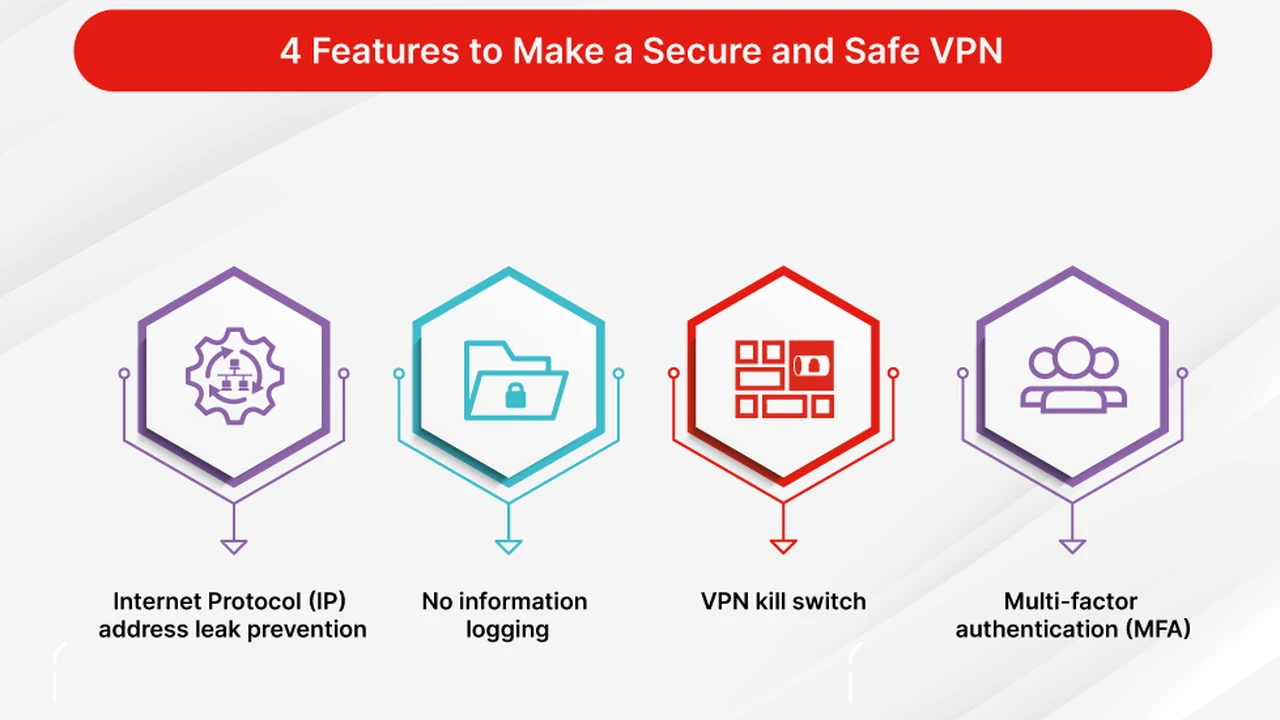
Strict No Logs Policy and Independent Audits for Privacy Assurance
A VPN's logging policy is critical. In high-risk regions, a VPN that logs your activity can be compelled to hand over that data to authorities. Therefore:
- Audited No-Logs Policy: The VPN provider should explicitly state a strict no-logs policy, meaning they do not record your IP address, browsing history, traffic destination, or connection timestamps. Crucially, this policy should be independently audited by a reputable third party to verify its claims.
- Jurisdiction: The country where the VPN company is legally based matters. Ideally, it should be outside the reach of intelligence alliances (like the 5/9/14 Eyes) and countries with mandatory data retention laws.
Obfuscation Technology and Stealth VPN for Bypassing Restrictions
In regions with heavy internet censorship or active VPN blocking, standard VPN connections might be detected and blocked. Obfuscation technology, also known as 'Stealth VPN,' is designed to make your VPN traffic look like regular internet traffic, thus bypassing detection:
- Scrambling Metadata: Obfuscation scrambles the metadata of your VPN connection, making it harder for deep packet inspection (DPI) systems to identify it as VPN traffic.
- Dedicated Obfuscated Servers: Some VPNs offer specific servers optimized for obfuscation, which are essential for users in highly restrictive environments.
Kill Switch and DNS Leak Protection for Uninterrupted Security
These features are vital to prevent accidental data exposure:
- Automatic Kill Switch: If your VPN connection drops unexpectedly, a kill switch immediately cuts off your internet access, preventing your real IP address and unencrypted data from being exposed. This is a must-have for high-risk scenarios.
- DNS Leak Protection: Your Domain Name System (DNS) requests can sometimes bypass the VPN tunnel, revealing your browsing activity to your ISP. A good VPN will have built-in DNS leak protection to ensure all DNS queries are routed through the encrypted tunnel.
- IPv6 Leak Protection: Similar to DNS leaks, IPv6 traffic can sometimes bypass the VPN. Ensure your chosen VPN offers protection against IPv6 leaks.
Additional Security Features for Comprehensive Protection
- Double VPN (Multi-Hop): Routes your traffic through two VPN servers in different locations, encrypting your data twice. This adds an extra layer of anonymity and makes tracing your connection significantly harder.
- Tor Over VPN: Combines the anonymity of the Tor network with the encryption of a VPN. Your traffic first goes through the VPN server, then through the Tor network, offering extreme anonymity, though often at the cost of speed.
- Dedicated IP Address: While not strictly a security feature, a dedicated IP can help avoid CAPTCHAs and blacklisting issues that sometimes arise from shared VPN IPs, which can be beneficial in certain high-risk contexts.
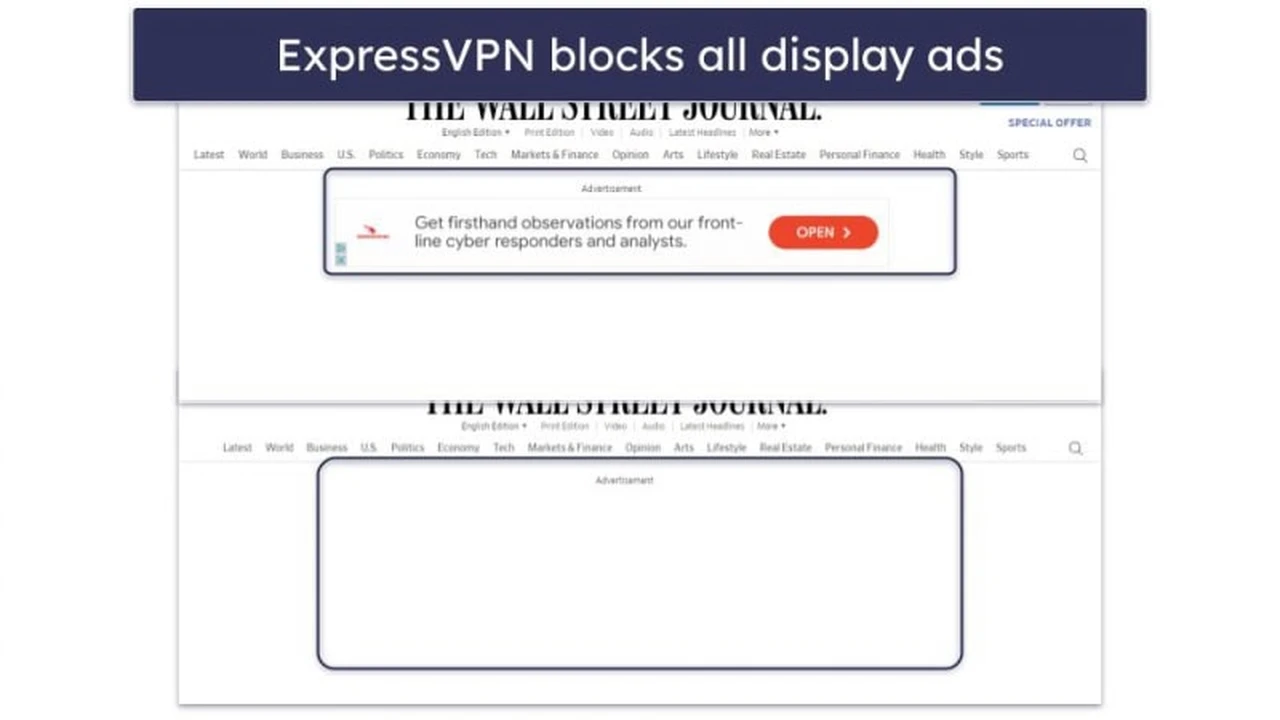
- Malware and Ad Blocker: Many VPNs now include built-in features to block malicious websites, ads, and trackers, further enhancing your security and privacy.
Top VPN Recommendations for High Risk Regions
Based on the critical features outlined above, here are some of the leading VPN providers that excel in providing security and privacy in high-risk environments:
ExpressVPN A Premium Choice for Robust Security and Speed
Why it's great for high-risk regions: ExpressVPN is consistently praised for its strong security features, audited no-logs policy, and excellent performance. It's based in the British Virgin Islands, a privacy-friendly jurisdiction. Their proprietary Lightway protocol offers a great balance of speed and security.
- Key Features: AES-256 encryption, Lightway, OpenVPN, IKEv2 protocols, automatic kill switch, DNS/IPv6 leak protection, audited no-logs policy, TrustedServer technology (RAM-only servers for enhanced security).
- Obfuscation: While not explicitly marketed as 'obfuscation,' ExpressVPN's servers are designed to intelligently evade detection, making it effective in restrictive countries.
- Server Network: Over 3,000 servers in 105 countries, including a strong presence in the USA and various Southeast Asian locations (e.g., Singapore, Thailand, Vietnam, Philippines).
- Use Cases: Bypassing censorship, secure communication, protecting against surveillance, streaming geo-restricted content.
- Pricing: Typically starts around $6.67/month for a 12-month plan, with a 30-day money-back guarantee.
NordVPN A Feature-Rich Option with Advanced Security Tools
Why it's great for high-risk regions: NordVPN offers a comprehensive suite of security features, including Double VPN, Onion Over VPN, and a robust kill switch. Their no-logs policy has been independently audited multiple times. They are based in Panama, another privacy-friendly jurisdiction.
- Key Features: AES-256 encryption, NordLynx (WireGuard-based), OpenVPN, IKEv2 protocols, kill switch, DNS leak protection, audited no-logs policy, Threat Protection (malware/ad blocker).
- Obfuscation: NordVPN offers dedicated 'Obfuscated Servers' specifically designed to bypass strict firewalls and VPN blocking, making it ideal for highly censored regions.
- Server Network: Over 6,000 servers in 61 countries, with extensive coverage in the USA and Southeast Asia (e.g., Vietnam, Singapore, Malaysia, Indonesia, Thailand).
- Use Cases: Extreme anonymity, bypassing government censorship, secure torrenting, protecting sensitive communications.
- Pricing: Starts around $3.99/month for a 2-year plan, with a 30-day money-back guarantee.
Surfshark An Affordable Powerhouse with Unlimited Connections
Why it's great for high-risk regions: Surfshark provides an impressive array of security features at a very competitive price, along with unlimited simultaneous connections. It's based in the Netherlands, which has strong privacy laws. Their no-logs policy has also been independently audited.
- Key Features: AES-256 encryption, WireGuard, OpenVPN, IKEv2 protocols, kill switch, DNS leak protection, audited no-logs policy, CleanWeb (ad/malware blocker), Bypasser (split tunneling).
- Obfuscation: Surfshark's 'NoBorders mode' automatically kicks in when it detects network restrictions, effectively obfuscating your VPN traffic.
- Server Network: Over 3,200 servers in 100 countries, with good coverage in the USA and Southeast Asia (e.g., Vietnam, Singapore, Thailand, Indonesia, Philippines).
- Use Cases: Protecting multiple devices, budget-conscious users in high-risk areas, bypassing censorship, secure streaming.
- Pricing: Starts around $2.29/month for a 2-year plan, with a 30-day money-back guarantee.
Proton VPN A Privacy-Focused Choice with Strong Transparency
Why it's great for high-risk regions: Proton VPN, from the creators of ProtonMail, is renowned for its strong commitment to privacy and security. It's based in Switzerland, a country with excellent privacy laws. They offer a transparent no-logs policy and open-source apps.
- Key Features: AES-256 encryption, WireGuard, OpenVPN, IKEv2 protocols, kill switch, DNS leak protection, audited no-logs policy, Secure Core (Double VPN through hardened servers), NetShield (ad/malware blocker).
- Obfuscation: Proton VPN offers 'Stealth' protocol, specifically designed to bypass censorship and VPN blocks, making it highly effective in restrictive environments.
- Server Network: Over 4,500 servers in 91 countries, with a decent presence in the USA and some Southeast Asian locations (e.g., Singapore, Malaysia).
- Use Cases: Journalists, activists, and anyone prioritizing extreme privacy and security, bypassing censorship.
- Pricing: Offers a limited free plan. Paid plans start around $4.99/month for a 2-year plan, with a 30-day money-back guarantee.
Private Internet Access (PIA) A Vast Network with Customizable Security
Why it's great for high-risk regions: PIA boasts one of the largest server networks and offers highly customizable security settings, allowing users to fine-tune their encryption levels. They have a proven no-logs policy in court multiple times. PIA is based in the USA, which can be a concern for some due to intelligence alliances, but their no-logs policy has held up.
- Key Features: AES-256/128 encryption, WireGuard, OpenVPN, IKEv2 protocols, kill switch, DNS/IPv6 leak protection, audited no-logs policy, MACE (ad/malware blocker), SOCKS5 proxy.
- Obfuscation: PIA offers Shadowsocks proxy integration, which can help obfuscate traffic, though it's not as integrated as some other providers' dedicated obfuscation features.
- Server Network: Thousands of servers in 91 countries, with extensive coverage in the USA and a growing presence in Southeast Asia (e.g., Singapore, Vietnam, Thailand).
- Use Cases: Users who want granular control over their security settings, torrenting, bypassing some restrictions.
- Pricing: Starts around $2.03/month for a 3-year plan, with a 30-day money-back guarantee.
Specific Considerations for the USA and Southeast Asia
VPN Usage in the USA Navigating Surveillance and Data Retention
Despite being a democratic nation, the USA's involvement in the Five Eyes alliance and its own surveillance programs (like PRISM) mean that privacy is a significant concern. Furthermore, ISPs in the USA can legally sell your browsing data. Therefore, for users in the USA:
- Audited No-Logs Policy is Paramount: Choose a VPN with a proven, independently audited no-logs policy to ensure your activities aren't recorded and can't be handed over.
- Strong Encryption: AES-256 encryption with secure protocols like WireGuard or OpenVPN is essential.
- Kill Switch and Leak Protection: These features are crucial to prevent accidental exposure of your IP address or DNS requests.
- Jurisdiction: While some top VPNs are based in the USA (like PIA), many users prefer VPNs based in privacy-friendly jurisdictions outside the 5/9/14 Eyes alliances to minimize legal risks.
- Server Locations: A VPN with a wide array of servers within the USA can help maintain speed while still encrypting your traffic and masking your IP from your ISP.
VPN Usage in Southeast Asia Bypassing Censorship and Geo-Restrictions
Southeast Asia is a diverse region with varying levels of internet freedom. Countries like Vietnam, Thailand, and Indonesia have implemented significant internet censorship, blocking access to social media, news sites, and political content. For users in Southeast Asia:
- Obfuscation Technology: This is often the most critical feature. VPNs with dedicated obfuscated servers or stealth modes (like NordVPN's Obfuscated Servers or Proton VPN's Stealth protocol) are highly recommended to bypass government firewalls.
- Strong Encryption and Protocols: As always, AES-256 encryption with WireGuard or OpenVPN is necessary.
- No-Logs Policy: Essential to protect your identity and activities from government surveillance.
- Server Network: A VPN with a good number of servers in or near Southeast Asian countries (e.g., Singapore, Malaysia, Hong Kong) can provide better speeds and access to regional content, while also offering servers further afield for bypassing local restrictions.
- Reliable Customer Support: In case of connection issues due to government blocking, responsive customer support can be invaluable.
Practical Tips for Maximizing VPN Security in High Risk Environments
Choosing the right VPN is only half the battle. How you use it also significantly impacts your security:
Always Use the Kill Switch and Verify Leak Protection
Ensure your VPN's kill switch is always enabled. Regularly test for DNS and IP leaks using online tools (e.g., dnsleaktest.com, ipleak.net) to confirm your VPN is functioning correctly and not exposing your data.
Choose the Right Protocol for Your Needs
While WireGuard offers speed, OpenVPN (especially TCP) can be more reliable in highly restricted networks due to its ability to mimic regular HTTPS traffic. Experiment with different protocols to find what works best for your specific situation.
Connect to Obfuscated Servers When Facing Restrictions
If you're in a country with heavy censorship, always connect to your VPN's obfuscated or stealth servers. These are specifically designed to bypass deep packet inspection and make your VPN traffic undetectable.
Avoid Free VPNs at All Costs in High Risk Scenarios
Free VPNs often come with significant compromises: weak encryption, logging of user data, intrusive ads, bandwidth limits, and even malware. In high-risk regions, using a free VPN is akin to having no VPN at all, and can even be more dangerous as your data might be sold or exposed.
Keep Your VPN Software Updated Regularly
Software updates often include critical security patches and performance improvements. Always keep your VPN client updated to the latest version to ensure you have the best protection against new threats.
Use Strong Passwords and Two-Factor Authentication (2FA)
Protect your VPN account itself with a strong, unique password and enable two-factor authentication (2FA) if available. This prevents unauthorized access to your VPN subscription.
Consider Using Tor Browser in Conjunction with Your VPN
For extreme anonymity, especially for sensitive activities, consider using the Tor browser in conjunction with your VPN (Tor over VPN). Connect to your VPN first, then launch Tor. This adds multiple layers of encryption and routing, making it incredibly difficult to trace your online activities.
Be Mindful of Your Digital Footprint Beyond the VPN
A VPN protects your internet connection, but it doesn't make you entirely anonymous if you're not careful. Avoid logging into personal accounts (like Google or social media) while performing sensitive activities. Use privacy-focused browsers (like Brave or Firefox with strong privacy settings) and search engines (like DuckDuckGo). Be cautious about what information you share online.
The Investment in a Secure VPN is an Investment in Your Freedom
In high-risk regions, the choice of a VPN is not just about accessing geo-restricted content; it's about safeguarding your fundamental rights to privacy, security, and freedom of information. While the initial cost of a premium VPN might seem like an expense, consider it an essential investment in your digital well-being. The peace of mind that comes from knowing your data is encrypted, your identity is protected, and your online activities are private is invaluable. By carefully selecting a VPN with robust security features, a proven no-logs policy, and effective obfuscation, you can navigate the complex digital landscapes of the USA and Southeast Asia with confidence and security.
:max_bytes(150000):strip_icc()/277019-baked-pork-chops-with-cream-of-mushroom-soup-DDMFS-beauty-4x3-BG-7505-5762b731cf30447d9cbbbbbf387beafa.jpg)